#Gootloader #Malware Resurfaces in #Google Ads for Legal Docs. Attackers target a familiar industry, law professionals, by hiding the infostealer in ads delivered via Google-based malvertising.
https://www.darkreading.com/cyberattacks-data-breaches/gootloader-malware-google-ads-legal-docs
Recent searches
Search options
#Gootloader
I've been waiting for this writeup for a long time. Great dive on #Gootloader: https://news.sophos.com/en-us/2025/01/16/gootloader-inside-out/
Of particular note is the 24-hour timeout for any IP that receives a Gootloader download prompt, frustrating research attempts. But the whole research process here is excellent.
We don't want to tell the entire story here, but the bottom line is this: #Gootloader is and remains one of the most convoluted #malware attack methods we've seen. Its social engineering ruse and the way it shapes itself to your desires still convince people to click its bad links.
Gootloader has been playing the long game, and winning, below most people's radar, for years. It shows no sign of slowing down or changing its methods. After all, it's a working formula.
/end
https://news.sophos.com/en-us/2025/01/16/gootloader-inside-out/

re: Long thread
When a site visitor follows one of the maliciously SEOed search terms (only on the first visit), the WordPress page redraws the #Gootloader content over the WordPress stuff that should appear there.
It retrieves the redrawn content by connecting to what we've called "the mothership" - a server hosted elsewhere that, in moments, delivers a bogus webpage with a dynamically-generated fictional Q&A.
It is a very convincing social engineering trick.
7/
re: Long thread
It also turns out that #Gootloader's operators have injected remote shells into a very common WordPress page that exists in most self-hosted WordPress installations. The HelloDolly.php file serves no purpose other than to insert random quotes from the eponymous song into backend admin pages.
It exists as a prototype of the ways WordPress can insert dynamically-generated content into a page, but it has been modified on some of the #Gootloader sites to contain a backdoor that gives them a backup method to execute commands on the server hosting the WordPress instance.
6/
re: Long thread
This research uncovered the fact that #Gootloader's operators dynamically add those IP address ranges to a block list stored inside the WordPress database, itself.
5/
re: Long thread
One way the #Gootloader operators conceal themselves in plain sight from the website's owner is by carefully controlling exactly how victims end up in their trap.
You can't get there by visiting the site URL; The request must contain a Referer header that shows you clicked a Google result.
And even if you stumble into their trap, if you try to do it a second time, #Gootloader will lock out not just your IP address, but the entire IP address range where you connect from, just for good measure.
4/
re: Long thread
Nobody knows exactly how the #Gootloader operators are finding and taking control over personal and business websites that use WordPress, but it's likely due to an earlier compromise of the site's administrator credentials, through #malware or #phishing. Stolen credentials for WordPress sites are a dime a dozen on the criminal underground.
The insidious nature of Gootloader means even the site's owners, who still have working admin passwords, cannot readily determine that the site is being misused for evil.
3/
Hi everyone, it's @threatresearch driving the X-Ops social media today to let you know about a story we just published, written by my colleague Gabor Szappanos.
Szapi has done significant research in the past into a #malware family called #Gootloader that (for years, now) uses malicious #SEO techniques to promote compromised websites into Google search results.
This research finally cracks wide open the mystery of how they manage to do that so effectively. It's a long read, but well worth the deep dive.
https://news.sophos.com/en-us/2025/01/16/gootloader-inside-out/
1/

"Gootloader’s Pivot from SEO Poisoning: PDF Converters Become the New Infection Vector"
"Visiting this WordPress site (surprise!), I found a form for uploading a PDF to convert it to a .DOCX file inside a .zip. But after passing certain checks—being from an English-speaking country and not having visited in the past 24 hours on the same class C subnet—users instead receive a .JS file inside the .zip rather than a genuine .DOCX."
https://gootloader.wordpress.com/2024/11/07/gootloaders-pivot-from-seo-poisoning-pdf-converters-become-the-new-infection-vector/
#GootLoader is still active and efficient
https://securityaffairs.com/165368/malware/gootloader-malware-is-still-active.html
#securityaffairs #hacking
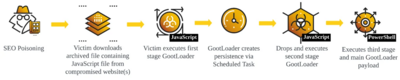
Finally finished reversing a new #GootLoader sample. Most #ThreatIntel I see suggests initial registry writes in support of the C2 payload, but it looks like they've done away with that and gone right to creating the Scheduled Tasks.
The DFIR Report posts from the future (26 February 2024). They provide a case study on a Gootloader infection stemming from an SEO-poisoned search result. 9 hours after infection, the malware deployed a Cobalt Strike beacon payload into the host's registry and executed it in memory. The threat actor deployed SystemBC to tunnel RDP access into the network, eventually compromising domain controllers, backup servers, and other key servers. IOC, Yara, Sigma rules, MITRE ATT&CK TTPs provided. https://thedfirreport.com/2024/02/26/seo-poisoning-to-domain-control-the-gootloader-saga-continues/
Current #GootLoader site, serving up malicious zip/js is hxxps://zoom.sleekdev.xyz/archive.php
Current #GootLoader site, serving up malicious zip/js is hxxps://www.ototo.com.cn/api.php
Current #GootLoader site, serving up malicious zip/js is hxxps://www.nilsjapan.com/api.php
@GossiTheDog @malware_traffic that Emma Hill is a busy, busy bee.
Soon to be the third anniversary of this blog. Virtually identical web template in the post. https://news.sophos.com/en-us/2021/03/01/gootloader-expands-its-payload-delivery-options/
#Gootloader #malware
Current #GootLoader site, serving up malicious zip/js is hxxps://w3bminds.com/blog.php
Super handy detection for #GootLoader and others: for some reason, they think it's cute to make scheduled tasks using a changed working directory and the DOS shortname of the executable. But since no human would stack books like this regular scheduled task does this, an explicit DOS shortname with a ~1 in the task execution is a fairly solid detection signal.
#ThreatIntel #GootLoader
@mttaggart I saw this fly by, any help?
Current #GootLoader site, serving up malicious zip/js is hxxps://thieuhoa.com.vn/blog.php



 decio
decio 