Released: #swad v0.1
Looking for a simple way to add #authentication to your #nginx reverse proxy? Then swad *could* be for you!
swad is the "Simple Web Authentication Daemon", written in pure #C (+ #POSIX) with almost no external dependencies. #TLS support requires #OpenSSL (or #LibreSSL). It's designed to work with nginx' "auth_request" module and offers authentication using a #cookie and a login form.
Well, this is a first release and you can tell by the version number it isn't "complete" yet. Most notably, only one single credentials checker is implemented: #PAM. But as pam already allows pretty flexible configuration, I already consider this pretty useful
If you want to know more, read here:
https://github.com/Zirias/swad










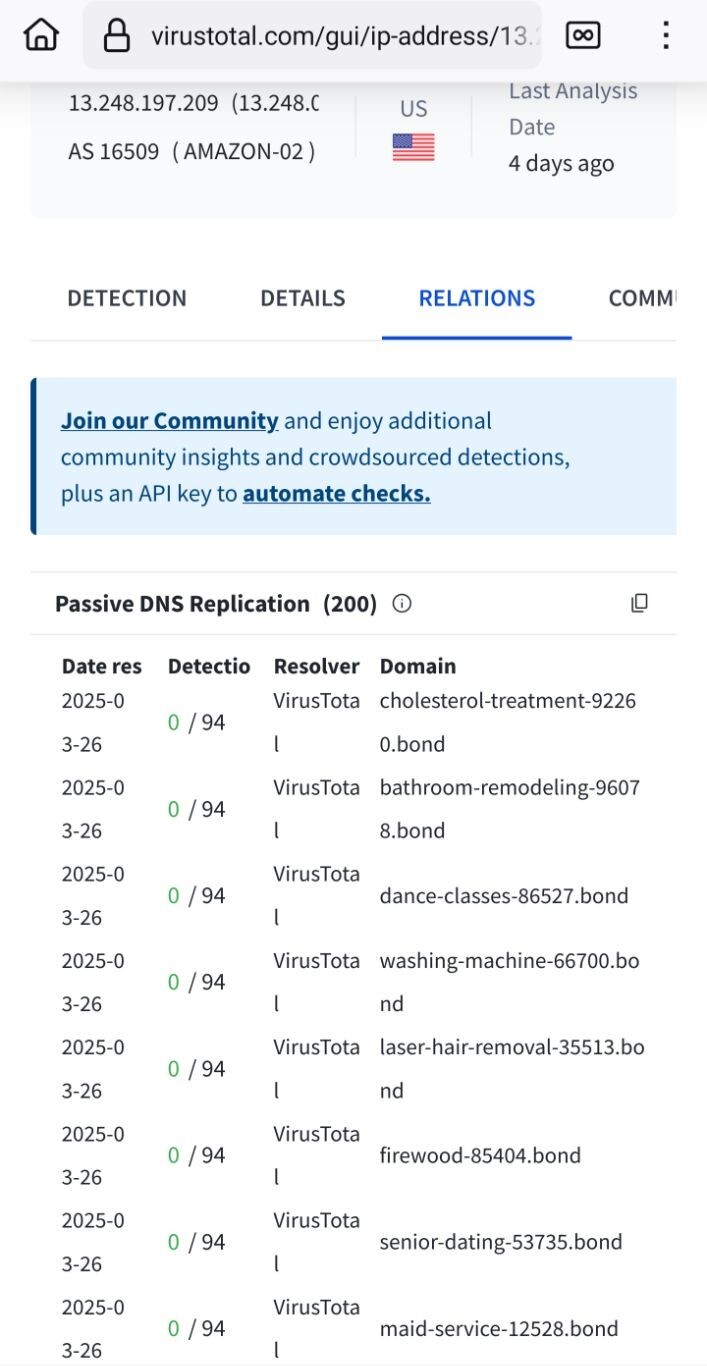
![Screenshot from part of https://www.virustotal.com/gui/ip-address/188.114.96.0/relations
showing domain names of malicious websites, like the following ones (do not visit them):
mondialrelay-client-fr[.]com
oxfun-rpcdebug.pages[.]dev
usps.paytollike[.]vip
at-tmailler.typedream[.]app
ycoficial[.]com
productreview.myappgurus[.]com
stonenumber[.]icu
api.sulek[.]dev
badaidrop[.]live Screenshot from part of https://www.virustotal.com/gui/ip-address/188.114.96.0/relations
showing domain names of malicious websites, like the following ones (do not visit them):
mondialrelay-client-fr[.]com
oxfun-rpcdebug.pages[.]dev
usps.paytollike[.]vip
at-tmailler.typedream[.]app
ycoficial[.]com
productreview.myappgurus[.]com
stonenumber[.]icu
api.sulek[.]dev
badaidrop[.]live](https://mastodon.bida.im/system/cache/media_attachments/files/114/228/921/865/845/638/small/3a2bfd5d1a9d1140.jpeg)


![Screenshot of https://www.virustotal.com/gui/domain/mailchimp-sso.com/relations
It shows that mailchimp-sso[.]com is "hosted" (actally proxied) by Cloudflare IP-addresses. Screenshot of https://www.virustotal.com/gui/domain/mailchimp-sso.com/relations
It shows that mailchimp-sso[.]com is "hosted" (actally proxied) by Cloudflare IP-addresses.](https://mastodon.bida.im/system/cache/media_attachments/files/114/222/237/296/353/072/small/edc9ce6cba026c73.jpeg)
![Screenshot of https://www.virustotal.com/gui/domain/mailchimp-sso.com/details
It shows that mailchimp-sso[.]com has a DV-certificate issued by "Google Trust Services". Screenshot of https://www.virustotal.com/gui/domain/mailchimp-sso.com/details
It shows that mailchimp-sso[.]com has a DV-certificate issued by "Google Trust Services".](https://mastodon.bida.im/system/cache/media_attachments/files/114/222/237/335/011/417/small/990cbd237e932735.jpeg)



